🕵️ Welcome to the Null404 DFIR CTF – FY25Q3
Sponsored by ArcLight6
🧭 Getting Started
Welcome to the Null404 DFIR Capture The Flag, a digital forensics challenge designed to test your investigation skills in a simulated enterprise breach scenario. This event is proudly sponsored by ArcLight6.
📦 Required Materials
Download the KAPE triage packages used throughout the competition:
Note: When downloading the Kape files, you may see the following message: "Google Drive can't scan this file for viruses. NULL404Q3CTF.7z (389 MB) is too large for Google to scan for viruses. Would you still like to download this file?" This is a standard Google Drive warning for large files. The file is safe to download and can be trusted.
Note: These packages are encrypted. The decryption password will be revealed in the first challenge when the CTF begins.
SHA256: a24544556739db319afb026881894e315adde26ad9382de28a405c0bb84a4daa - NULL404Q3CTF.7z
Rules of Engagement
- No Brute Forcing: Do not brute-force flags, endpoints, or login pages. All challenges are solvable with analysis and reasoning.
- No Attacking the Infrastructure: Do not run scans, exploit vulnerabilities, or attempt to disrupt the CTF platform.
- No Sharing Flags: Work on your own or with your team. Sharing answers or solutions with other teams is not allowed.
- AI: If you choose to use any AI platform, please do so at your own discretion. Make sure you continue to learn and have fun along the way.
- No Automation or Scripts: Unless a challenge explicitly permits it, do not use automated tools to interact with the platform.
- Be Respectful: Treat all participants with respect and uphold the spirit of healthy competition.
- Report Issues: If you discover a bug or have questions, contact the organizers. Do not exploit platform flaws.
- Have Fun & Learn: The main goal is to develop your DFIR skills. Enjoy the challenges and grow!
🚀 How to Begin Analysis
- 📂 Unzip the triage archive using your preferred archive tool (e.g., 7-Zip). Remember, it is password protected.
- 🔍 Analyze the files using tools like the Eric Zimmerman Suite.
- 🧠 Focus your investigation on event logs, registry hives, browser activity, and file system metadata.
- Windows Forensic Analysis
- Memory Forensics
- Malware Analysis
- Network Forensics
- And more
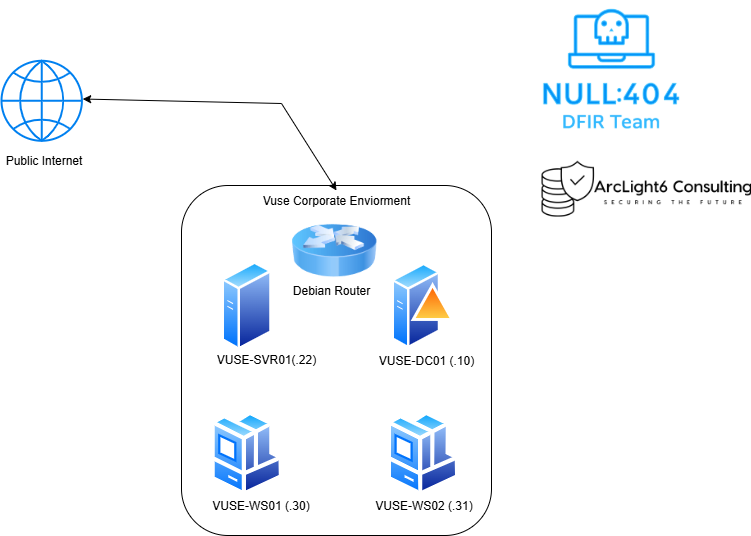
- VUSE-DC01 (10.3.10.10) – Domain Controller
- VUSE-SVR01 (10.3.10.22) – SMB File Server
- VUSE-WS01 (10.3.10.30) – User Workstation
- VUSE-WS02 (10.3.10.31) – User Workstation
- 📁 Master File Table (MFT)
- 🕒 Prefetch files
- 📑 Event Logs (EVTX)
- 🌐 Browser History
- 🧠 AmCache and ShimCache
- 🔍 Registry Hives (SAM, SYSTEM, SOFTWARE, NTUSER.DAT)
- 🚀 Scheduled Tasks
- 🔧 Services and Startup Items
- 💬 Recent Files and Jump Lists
- Analyze triaged artifacts to answer questions and earn points
- Track the attacker’s movements and behavior
- Reconstruct the timeline of compromise
- Identify persistence mechanisms and lateral movement
- Attribute the attack and determine the method of exfiltration
🔍 Quick Reference guides:
For guidance during your investigation, check out these comprehensive DFIR cheat sheets:
DFIR Training Cheat Sheets & Infographics
Topics include:
Use these resources to help uncover critical evidence and guide your analysis.
🌐 Network Overview
The environment simulates a small enterprise network impacted by a targeted attack. You will encounter systems such as:
The diagram below provides a high-level view of the Vuse Corporation network topology:
📂 Artifacts Included
The triage packages collected via KAPE contain various forensic artifacts, including:
🏆 Objectives
Use your DFIR skills, follow the artifacts, and expose the threat actor’s playbook.
— The Null404 DFIR Team